HACKTHEBOX - ROGUEONE

Your SIEM generated multiple alerts in less than a minute, indicating potential C2 communication from Simon Stark's workstation. Despite Simon not noticing anything unusual, the IT team had him share screenshots of his task manager to check for any unusual processes. No suspicious processes were found, yet alerts about C2 communications persisted. The SOC manager then directed the immediate containment of the workstation and a memory dump for analysis. As a memory forensics expert, you are tasked with assisting the SOC team at Forela to investigate and resolve this urgent incident.
1 zip of 1.3GB containing a 5.5 GB memory dump in .mem format. This dump appears to come from a Windows machine.
Content Analysis
Let's analyze the processes running on the dumped machine with volatility.
Volatility is a very useful forensic tool for analyzing Linux and Windows memory dumps. For this writeup, we will use the latest version of volatility to date, version 3.
This means that when vol.py is mentioned, it actually refers to the volatility3 executable.
Link to download volatility3: https://github.com/volatilityfoundation/volatility3
python3.11 vol.py -f ../20230810.mem windows.pstree.PsTree
PID PPID ImageFileName Offset(V) Threads Handles SessionId Wow64 CreateTime ExitTime
<SNIP>
** 7436 7400 explorer.exe 0x9e8b8c4d2080 75 - 1 False 2023-08-10 11:14:07.000000 N/A
*** 5864 7436 WinRAR.exe 0x9e8b92bdb0c0 5 - 1 False 2023-08-10 11:20:21.000000 N/A
**** 1576 5864 msedgewebview2 0x9e8b8b4cc080 47 - 1 False 2023-08-10 11:20:21.000000 N/A
***** 6084 1576 msedgewebview2 0x9e8b8b0f1080 19 - 1 False 2023-08-10 11:20:25.000000 N/A
***** 2728 1576 msedgewebview2 0x9e8b8cf97080 7 - 1 False 2023-08-10 11:20:21.000000 N/A
***** 2284 1576 msedgewebview2 0x9e8b8b8dc080 14 - 1 False 2023-08-10 11:20:25.000000 N/A
***** 1552 1576 msedgewebview2 0x9e8b8aa85080 8 - 1 False 2023-08-10 11:20:25.000000 N/A
***** 1616 1576 msedgewebview2 0x9e8b8a74f080 22 - 1 False 2023-08-10 11:20:25.000000 N/A
*** 936 7436 svchost.exe 0x9e8b8cd89080 0 - 1 False 2023-08-10 11:22:31.000000 2023-08-10 11:27:51.000000
**** 8260 936 cmd.exe 0x9e8b8afda300 2 - 1 False 2023-08-10 11:27:15.000000 N/A
***** 1668 8260 conhost.exe 0x9e8b92c65300 3 - 1 False 2023-08-10 11:27:15.000000 N/A
*** 9580 7436 SecurityHealth 0x9e8b90135340 1 - 1 False 2023-08-10 11:14:25.000000 N/A
*** 9712 7436 vmtoolsd.exe 0x9e8b8cbd5080 9 - 1 False 2023-08-10 11:14:26.000000 N/A
*** 2776 7436 RamCapture64.e 0x9e8b8aa66080 5 - 1 False 2023-08-10 11:31:52.000000 N/A
**** 9816 2776 conhost.exe 0x9e8b91cda080 6 - 1 False 2023-08-10 11:31:52.000000 N/A
*** 6812 7436 svchost.exe 0x9e8b87762080 3 - 1 False 2023-08-10 11:30:03.000000 N/A
**** 4364 6812 cmd.exe 0x9e8b8b6ef080 1 - 1 False 2023-08-10 11:30:57.000000 N/A
***** 9204 4364 conhost.exe 0x9e8b89ec7080 3 - 1 False 2023-08-10 11:30:57.000000 N/A
We notice a svchost.exe process (PID 936 and PID 6812) that has cmd.exe as a child process. This seems suspicious. To confirm the suspicion, we can dump the command history executed on the machine:
python3.11 vol.py -f ../20230810.mem windows.cmdline.CmdLine
6812 svchost.exe "C:\Users\simon.stark\Downloads\svchost.exe"
4364 cmd.exe C:\WINDOWS\system32\cmd.exe
9204 conhost.exe \??\C:\WINDOWS\system32\conhost.exe 0x4
9784 SearchFilterHo "C:\WINDOWS\system32\SearchFilterHost.exe" 0 764 820 828 8192 824 808
2776 RamCapture64.e "C:\Users\simon.stark\Desktop\BelkaSoft Live RAM Capturer\BelkaSoft Live RAM Capturer\RamCapture64.exe"
9816 conhost.exe \??\C:\WINDOWS\system32\conhost.exe 0x4
We see that the location of svchost.exe is not "standard" (C:\Users\simon.stark\Downloads\svchost.exe). There is a good chance that this process is a malicious process trying to impersonate the authentic svchost.exe process (https://en.wikipedia.org/wiki/Svchost.exe)
T1: Please identify the malicious process and confirm process id of malicious process: 6812
T2: The SOC team believes the malicious process may have spawned another process which enabled the threat actor to execute commands. What is the process ID of that child process: 4364
Note that we notice the other process seems legitimate. Its location is standard (C:\WINDOWS\System32\svchost.exe) and corresponds to the authentic service:
9088 svchost.exe C:\WINDOWS\System32\svchost.exe -k wsappx -p -s ClipSVC
6344 svchost.exe C:\WINDOWS\system32\svchost.exe -k defragsvc
1244 svchost.exe C:\WINDOWS\System32\svchost.exe -k LocalSystemNetworkRestricted -p -s DsSvc
8260 cmd.exe C:\WINDOWS\system32\cmd.exe
1668 conhost.exe \??\C:\WINDOWS\system32\conhost.exe 0x4
We can then dump this executable for analysis. To do this, we first need to "scan" the dump's files with volatility to find the virtual address of the corresponding file:
python3.11 vol.py -f ../20230810.mem windows.filescan.FileScan | grep 'svchost.exe'
<SNIP>
0x9e8b909045d0 \Users\simon.stark\Downloads\svchost.exe 216
</SNIP>
Now that we have the virtual address of the executable we can dump it:
python3.11 vol.py -o /home/victorhin0/HTB/SHERLOCKS/ROGUEONE -f ../20230810.mem windows.dumpfiles.DumpFiles --virtaddr 0x9e8b909045d0
Volatility 3 Framework 2.5.2
Progress: 100.00 PDB scanning finished
Cache FileObject FileName Result
DataSectionObject 0x9e8b909045d0 svchost.exe Error dumping file
ImageSectionObject 0x9e8b909045d0 svchost.exe file.0x9e8b909045d0.0x9e8b957f24c0.ImageSectionObject.svchost.exe.img
The .img file is actually the svchost.exe
We can calculate its md5 (to compare with threat intel such as VirusTotal)
md5sum svchost.exe
5bd547c6f5bfc4858fe62c8867acfbb5 svchost.exe
T3 : The reverse engineering team needs the malicious file sample to analyze. Your SOC manager instructed you to find the hash of the file and then forward the sample to reverse engineering team. What's the md5 hash of the malicious file?: 5bd547c6f5bfc4858fe62c8867acfbb5
We have confirmed that there is indeed a malicious process on the dumped machine. We then need to identify the C2C (Command and Control) server. To do this we will list the connections made on the machine:
python3.11 vol.py -o /home/victorhin0/HTB/SHERLOCKS/ROGUEONE -f ../20230810.mem windows.netscan > ../netlist.txt
We then have a text file with the list of incoming/outgoing connections established, and "pending" connections (like an HTTP server with no active connections). We can filter the results to match the malicious PID (here 6812):
cat ../netlist.txt | grep 6812
0x9e8b8cb58010 TCPv4 172.17.79.131 64254 13.127.155.166 8888 ESTABLISHED 6812 svchost.exe 2023-08-10 11:30:03.000000
We then identify that the C2C server is 13.127.155.166 and the port used is 8888
T4 : In order to find the scope of the incident, the SOC manager has deployed a threat hunting team to sweep across the environment for any indicator of compromise. It would be a great help to the team if you are able to confirm the C2 IP address and ports so our team can utilise these in their sweep. : 13.127.155.166:8888
T5 : We need a timeline to help us scope out the incident and help the wider DFIR team to perform root cause analysis. Can you confirm time the process was executed and C2 channel was established? 10/08/2023 11:30:03
Now, we will find the memory offset of the malicious process. For this, we can list the running processes on the machine:
python3.11 vol.py -f ../20230810.mem windows.pslist.PsList | grep 6812
6812 7436 svchost.exe 0x9e8b87762080 3 - 1 False 2023-08-10 11:30:03.000000 N/A Disabled
4364 6812 cmd.exe 0x9e8b8b6ef080 1 - 1 False 2023-08-10 11:30:57.000000 N/A Disabled
T6 : What is the memory offset of the malicious process? : 0x9e8b87762080
Finally, we upload the md5 corresponding to the malicious file to VirusTotal: https://www.virustotal.com/gui/file/eaf09578d6eca82501aa2b3fcef473c3795ea365a9b33a252e5dc712c62981ea/details
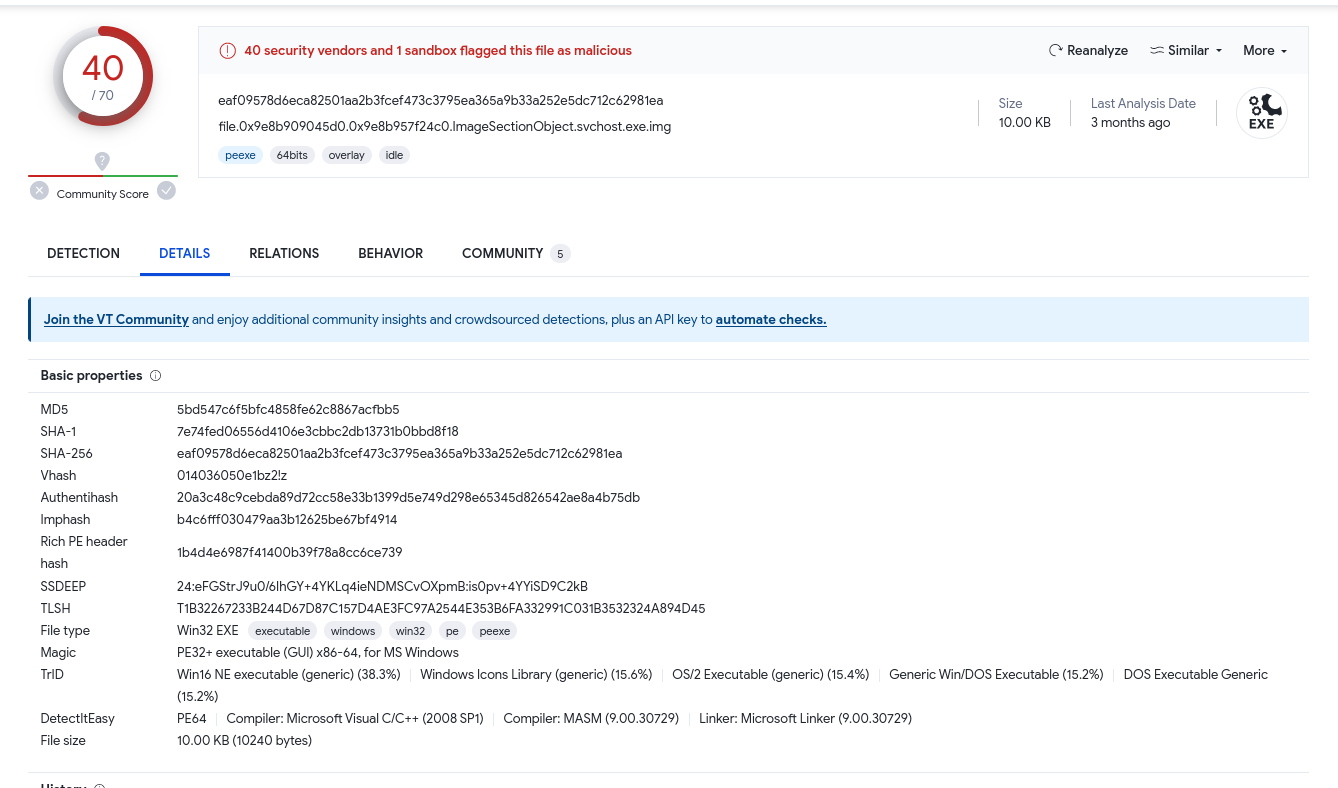
We notice that the file is well detected by most AV engines. We find the date of the first submission
T7 : You successfully analyzed a memory dump and received praise from your manager. The following day, your manager requests an update on the malicious file. You check VirusTotal and find that the file has already been uploaded, likely by the reverse engineering team. Your task is to determine when the sample was first submitted to VirusTotal : 10/08/2023 11:58:10
Useful References
https://andreafortuna.org/2017/07/10/volatility-my-own-cheatsheet-part-3-process-memory/